GOODBYE PASSWORDS, HELLO SECURITY!

GOODBYE PASSWORDS, HELLO SECURITY!
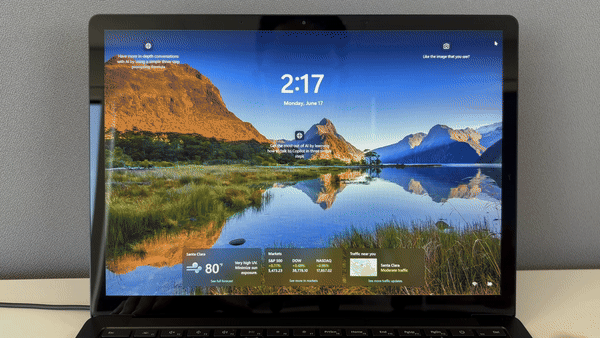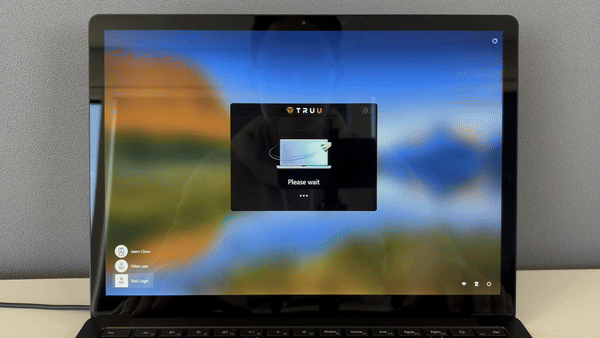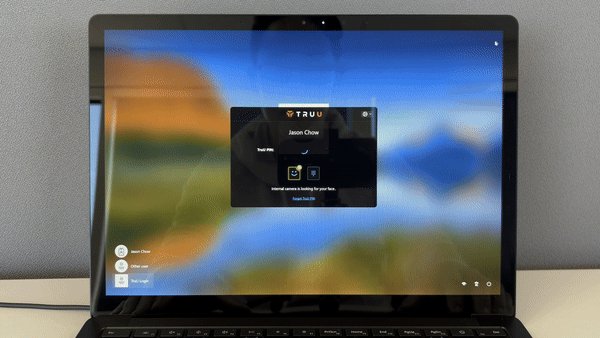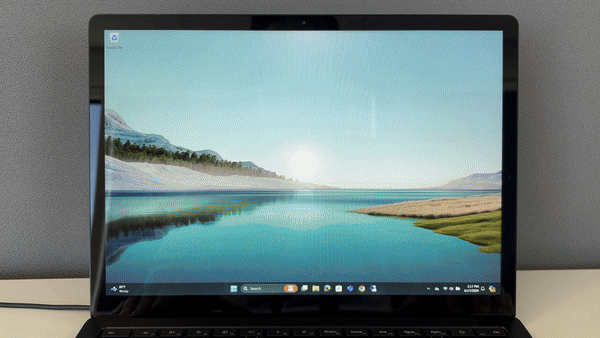
Compromised devices pose a significant security threat. TruU ensures that devices your employees use meet your policy requirements and are not jailbroken, biometric-modified, or otherwise compromised. Combined with assessing the environment, you can trust the session without trusting the device.
TruU extends your existing SSO investments by enabling truly password-less login experiences to your federated resources. Choose from a variety of supported Identity Providers (IdP) including Microsoft EntraID, Okta, PingFederate, ForgeRock, Google Cloud Identity, Oracle Access Management and more. TruU integrates with your Identity Provider using standards like SAML and OpenID Connect or partner certified integrations to ensure long term support and compatibility.
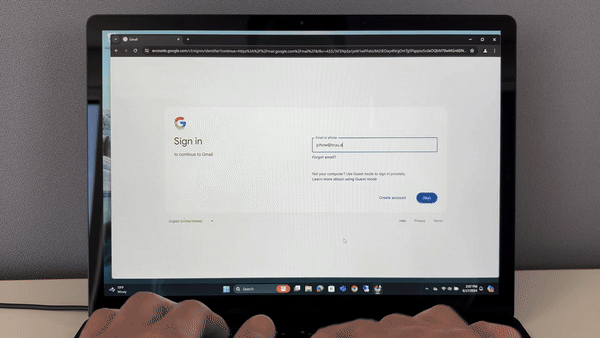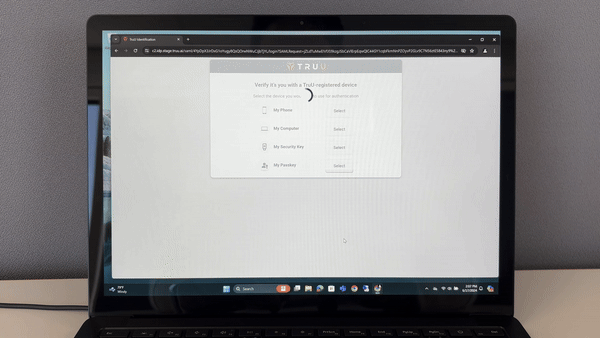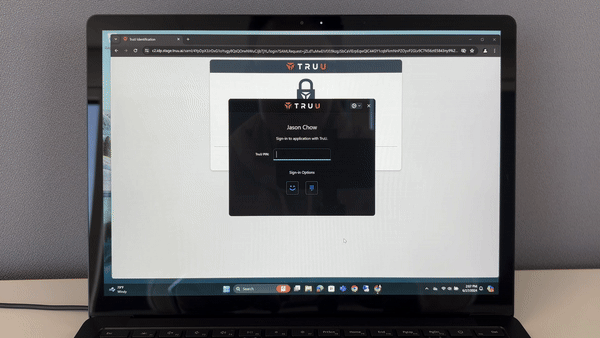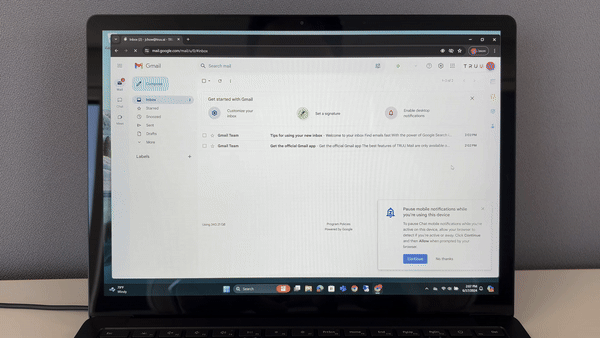
TruU also enables secure password-less access to your remote Windows resources. With the TruU Platform Authenticator for Windows, use your standard user account or your (-a) administrator account for strong authentication across your server infrastructure.
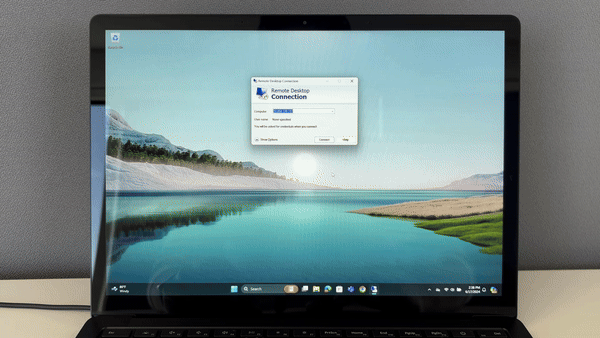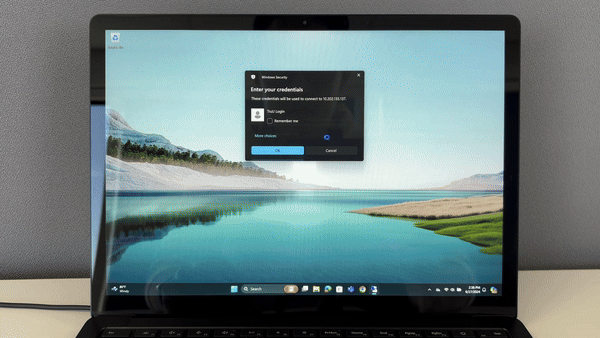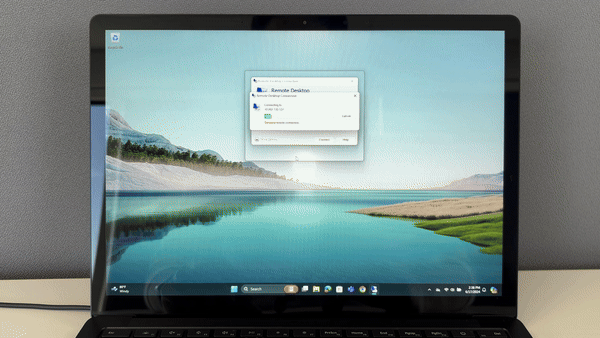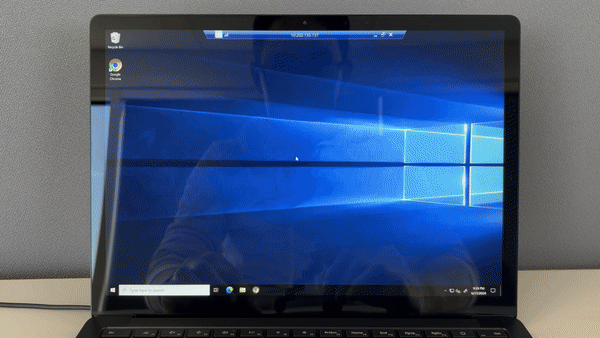
Use TruU when access remote Linux, Unix or AIX servers in your environment. TruU’s Pluggable Authentication Modules (PAM) eliminate the use of SSH keys and password vaults, and instead, provides strong password-less authentication across your server infrastructure.
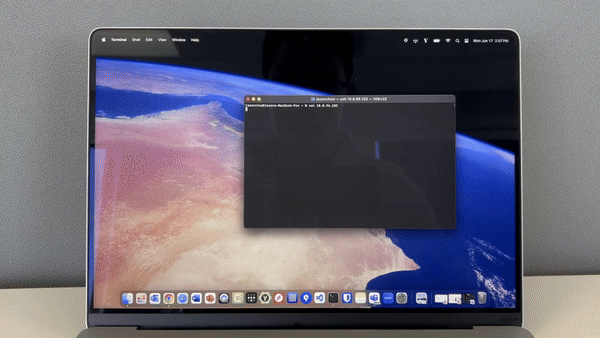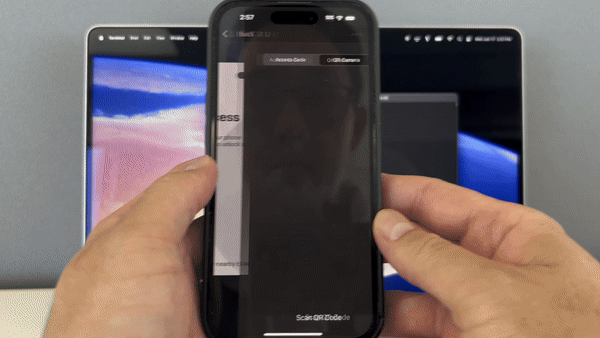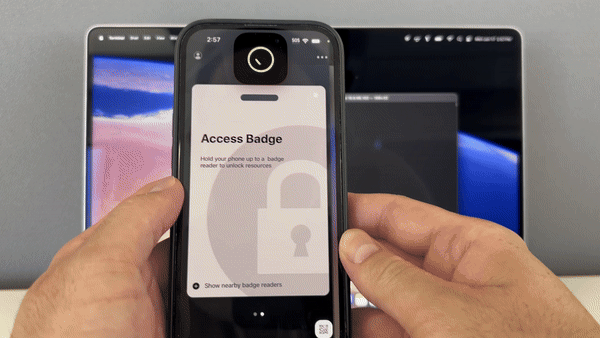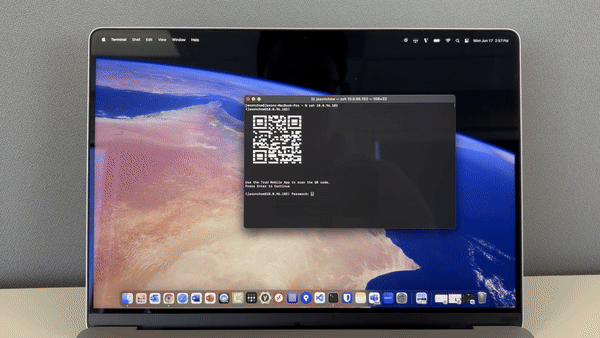
TruU’s Enterprise Passkey support removes the limitation of needing to use TruU software. Using just a modern computer, browser or security key, users can securely access corporate resources without a password.
Logins to Wi-Fi and other network devices require strong authentication. TruU integrates with network devices using industry standards such as RADIUS or SAML in order to provide a truly password-less login experience across your organization.
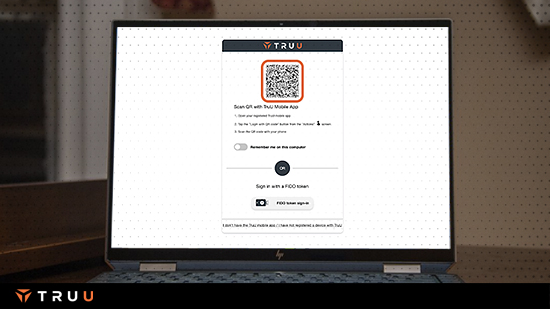
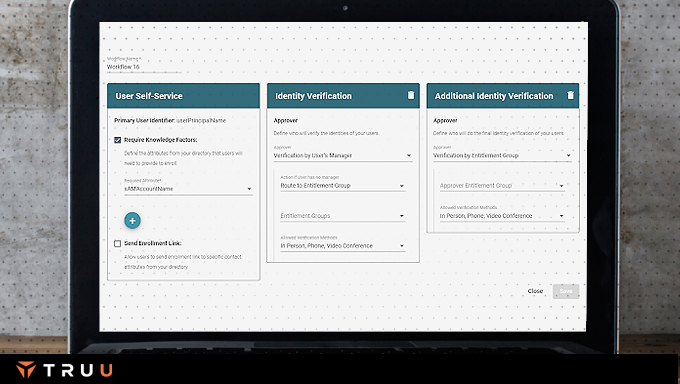
FIDO solutions ensure that the person who enrolled a key or smartphone is the person that later accesses a resource, but with email being the source of that enrollment, the possibility exists for impersonation. TruU goes a step further in its enrollment options to ensure identity is proofed and highly verified at the time of employee onboarding. TruU leverages policies, workflows and self-proofing to cater to any enterprise scenario and NIST requirement
TruU supports a variety of authenticator form-factors to accommodate a broad set of use cases. Use a smartphone, FIDO compliance security key or FIDO compliant wearables to access digital and physical resources across environments such as security sensitive areas, lab production, cleanroom environments and limited mobile/wi-fi coverage areas
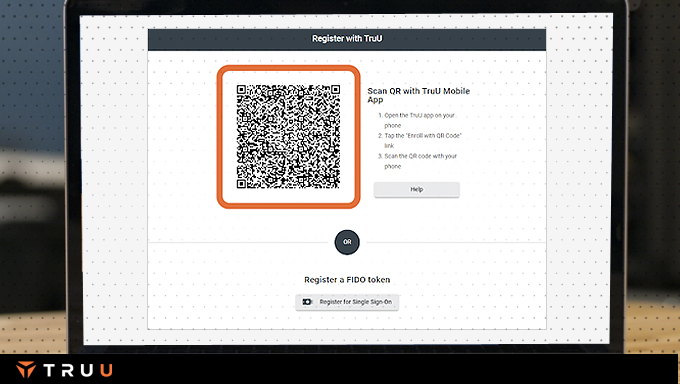
Losing or otherwise replacing a phone does not have to result in inability to access resources and negatively impacting productivity. Your users can quickly on-board their identity on their new device without having to contact help desk, while following your prescribed policies and workflows.
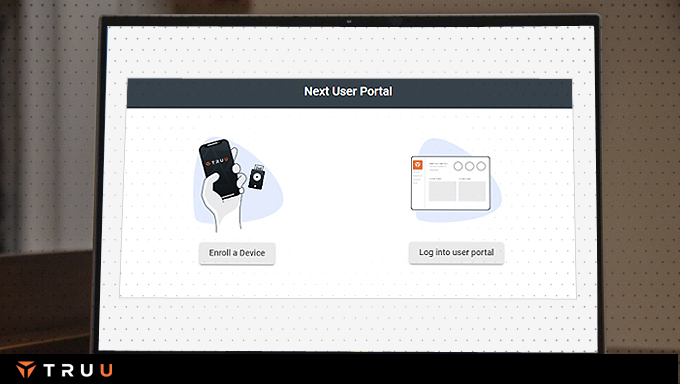
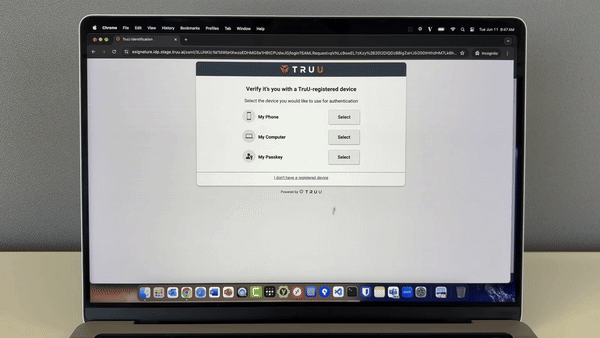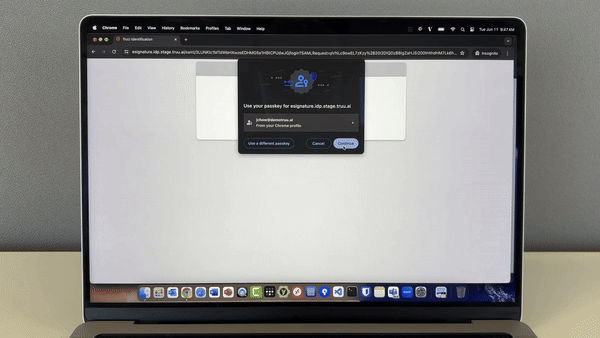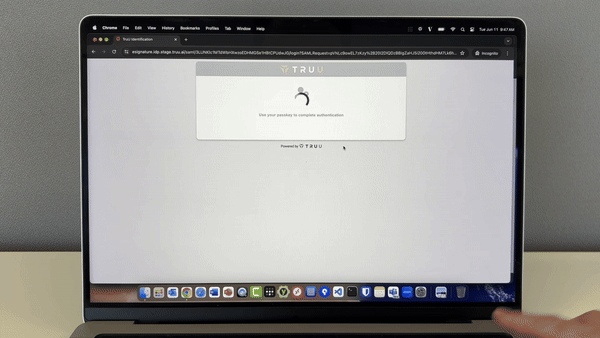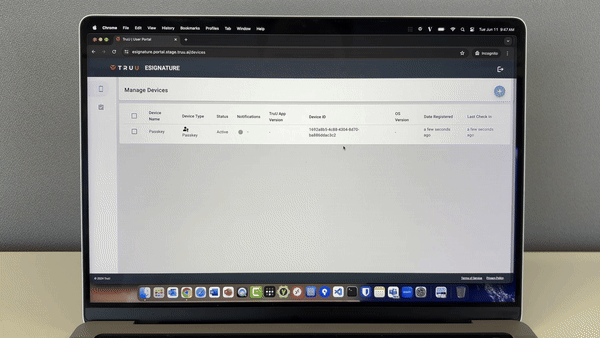
Free up your help desk to tackle real problems by enabling your users to onboard by themselves. TruU’s self-service portal enables end users to enroll and manage their devices from anywhere based on your security requirements. Combined with user optimized interfaces to workstations, applications and other TruU enabled resources, self-service onboarding and recovery has never been easier.
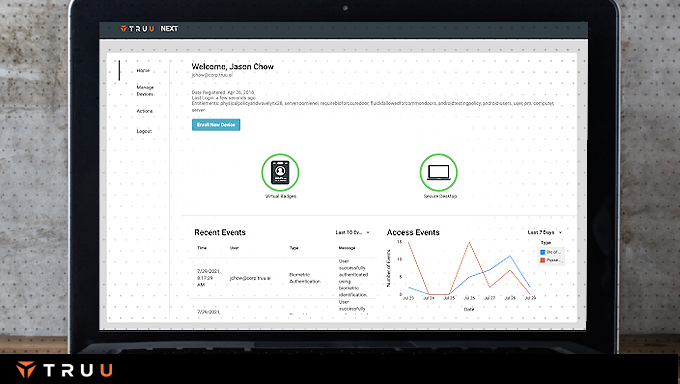
TruU’s pre-built integrations allow you to quickly realize value across a variety of use cases – digital and physical. TruU integrations are based on industry standards or partner certified adapters to ensure easy deployment, long term support and compatibility across heterogeneous environments.
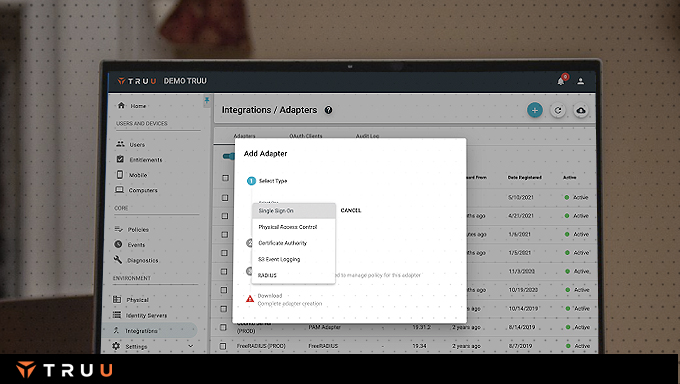
The TruU Admin Console allows you to manage your entire TruU deployment from anywhere and on any device with an internet connection. You can upgrade, roll-back or restart TruU software with the click of a button, view health indicators and logs and run diagnostics all from a single pane of glass.
TruU dashboards answer questions like: “who is accessing a resource?”, “what resource are they accessing?”, “when did they access the resource?” and “how are they accessing the resource?”. Dashboards help you monitor the usage and adoption of TruU as you move away from passwords across your environment.
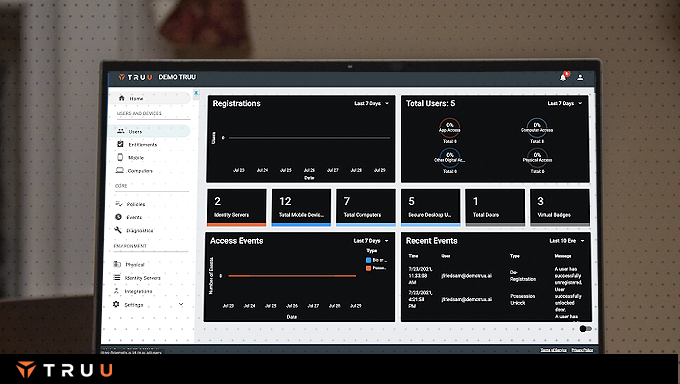
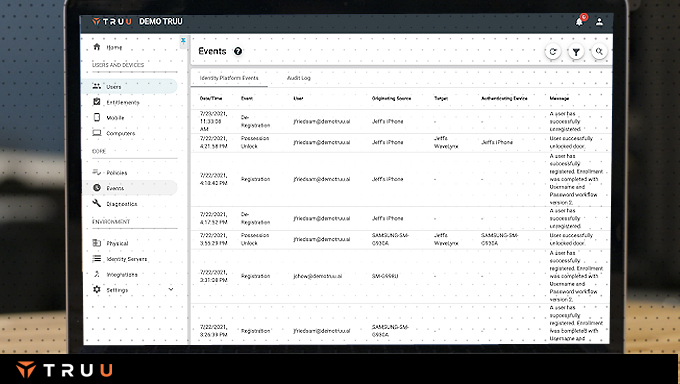
Whether it’s on-boarding, off-boarding, successful logins or login failures, TruU provides near real-time event streams for better visibility into your environment. You can also export these events to your SIEM for more centralized monitoring and alerting by your Security and Operations Control (SOC) team.
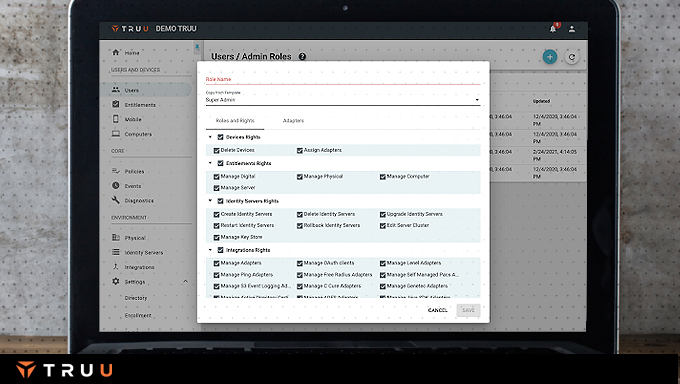
The TruU Admin Console is the command center for managing access across your organization. TruU’s role-based-access controls allows you to choose from a set of pre-built roles or build your own custom roles that limit access within your TruU Admin Console at a very granular level. Grant these roles to a single user or a group of users within your environment.
Whether it’s on-boarding, off-boarding, successful logins or login failures, TruU provides near real-time event streams for better visibility into your environment. You can also export these events to your SIEM for more centralized monitoring and alerting by your Security and Operations Control (SOC) team.
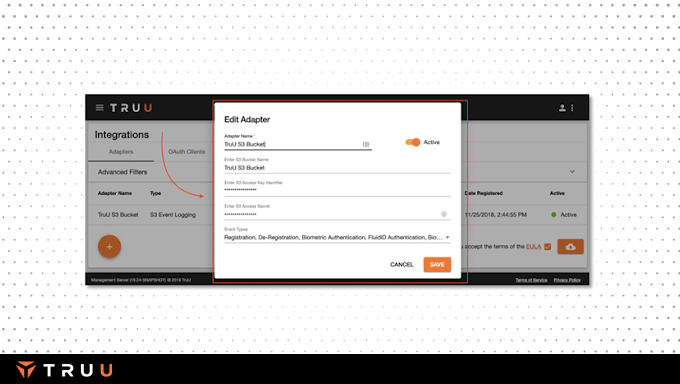
TruU is architected on an API-first model so most any functionality in the management portal can be accessed programmatically. Most commonly customers do things like automating user offboarding by tying into systems like SailPoint
TruU provides SDKs in 2 main scenarios: complete app customization to fit any enterprise experience, and account federation of apps which currently are not federated.
With TruU, you no longer need to provision multiple badges to accommodate multiple standalone physical access control systems in your environment. Virtual badges are automatically provisioned to the TruU mobile app and enable seamless physical access in place of a badge.

Use the TruU mobile app to require biometric verification for physical access to secure rooms or doors that are protecting more sensitive resources. Policy enforcement is configured in TruU while your existing physical access control system policies remain untouched.

Compromised devices and endpoints pose a significant security threat. TruU ensures that appliances your employees use meet your policy requirements and are not jailbroken/rooted, biometrics have not changed since enrollment, or otherwise compromised. Combined with assessing the environment, you can trust the session without trusting the device.
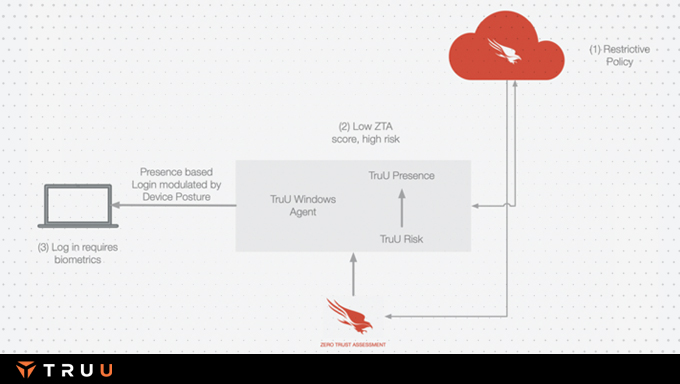
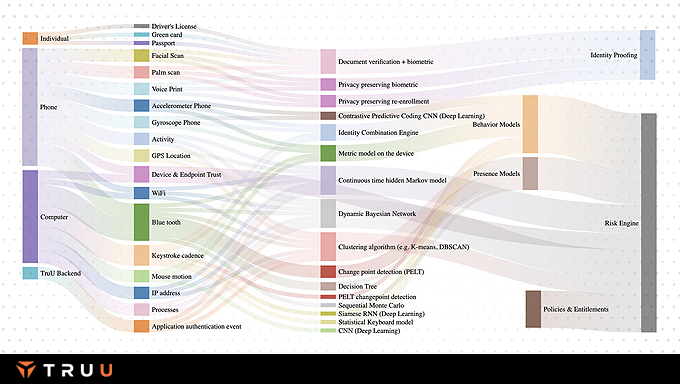
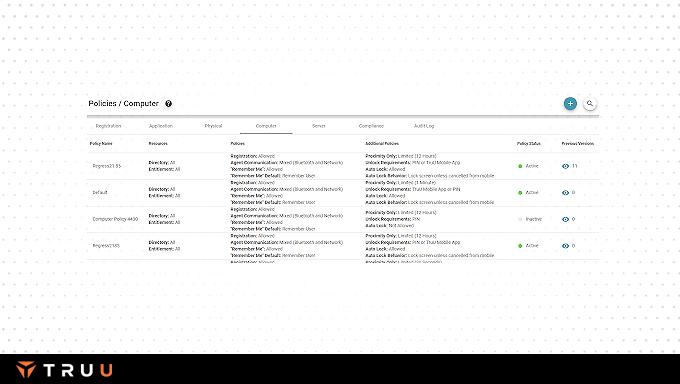
Policy engine gives an admin fine grain control over a user access to the entitled assets depending on behavioral, presence, and risk models.
TruU runs behavioral models on devices, endpoints, and TruU cloud that continuously monitor a user’s behavior and actions and create a measure of user identity that is used by the risk engine in making decisions.
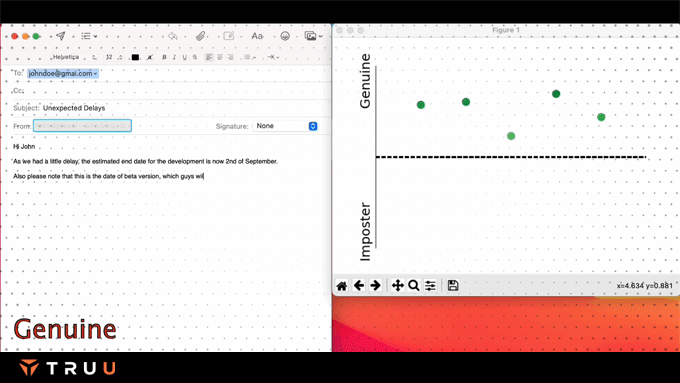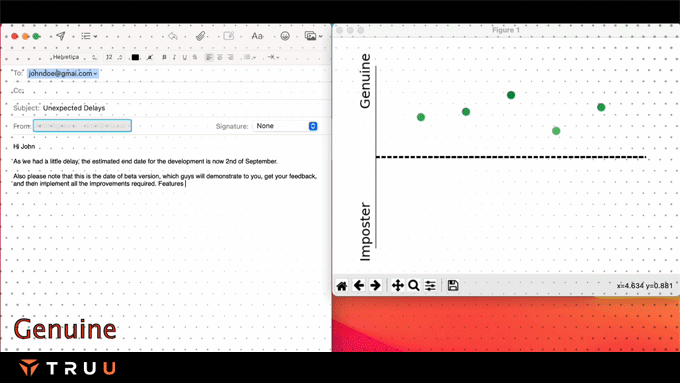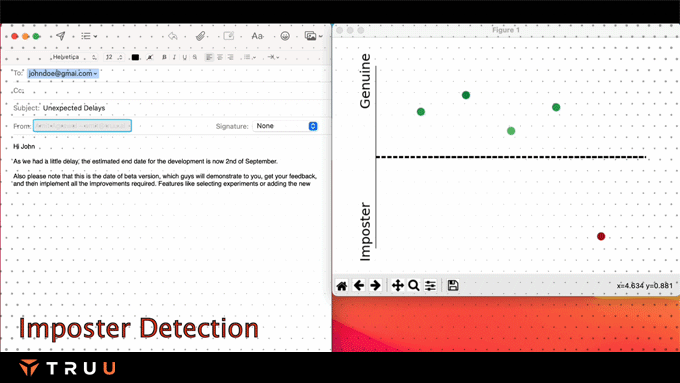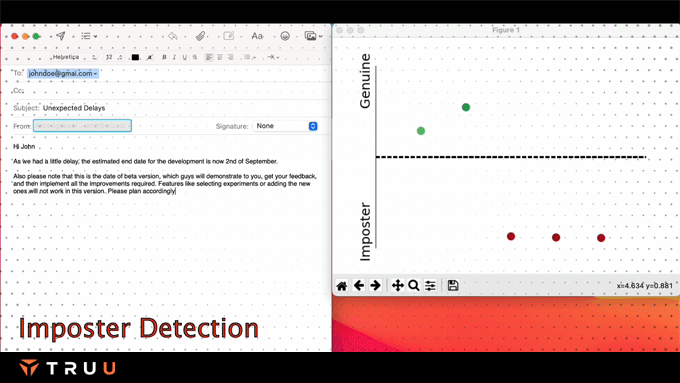
TruU’s presence models assess the risk posed by the separation between the authenticated asset and the authenticating entity and use that in the risk engine.
A user’s behavior patterns in space, time, or compared to peers are used to create a risk context that modulates the access granted in the TruU’s adaptive risk engine